Change SSH Port from Default for CentOS Security Improvement
The Secure Shell (SSH) is used to access a CentOS Server from another computer. For example when accessing a Virtual Private Server (VPS) to perform configuration changes. CentOS and other Linux versions are a common option for a VPS operating system. This tutorial provides details on changing the SSH default port number for a CentOS server.
This tutorial assumes that you can access the terminal for the CentOS server. If accessing a remote server the service provider will have connection details (e.g. terminal access via a control panel). If SSH is your only access point then be very careful not to lock yourself out. (In which case a support call to the remote service provider may be required.) If in doubt leave the port at the default setting of 22. Any changes that cause issues are your responsibility so only proceed if confident. If required you can practice on a local VM.

Reducing the Size of the Target for Hackers
As soon as a computer or device is connected to the Internet it becomes a target for bots or hackers trying to find weaknesses. Despite all the years of computer hacking software developers still keep to default settings. For example nearly all systems use the default port 22 for the secure shell (SSH). Why not randomise the port number? As long as the admin configuring the machine knows the port number then it can be given out on a need to know basis. Instead operating system (OS) developers just stick to port 22 for SSH, making it easier for bots to try and brute force in. So if the OS won't give SSH a different port number on install, change it yourself.
Help Harden a CentOS Server, Change SSH Port from Default Port Number 22
Here is the summary of the process to change SSH port from default port number 22. It involves an edit of the SSH configuration file to modify SSH port number (the configuration file is sshd_config). Then updating SELinux and firewalld (or iptables). This process is done to help harden CentOS against the less skilled hackers.
List of Steps to Change the CentOS SSH Port Number
The following are the steps to be performed to change default SSH port number on CentOS:
- Login to the CentOS server.
- Back up then edit the /etc/ssh/sshd_config file.
- Add the line Port XXXX to the file, where XXXX is the new port number.
- Update the SELinux policy for the new SSH port.
- Update the iptables (CentOS 6) or firewalld (CentOS 7) firewall rule for the new SSH port.
- Restart the services or the server.
- Check the changes worked by connecting on the new port.
Practice and Keep A Back Up
It is recommended to practice the detailed instructions that follow on a local test environment before doing it on a live machine. This ensures familiarity with the process and reduces the risk of making mistakes on a live server. CentOS can be configured on a local Virtual Machine (VM) to practice these changes. For a remote VPS if you make a mistake reconfiguring the SSH port you may not be able to connect to it. It will require resetting via your service provider's control panel. Always ensure you have a backup of any data that needs to be kept in the event the VPS needs to be reset. If SSH is the only option for configuration of a remote VPS consider other hardening options first, for example adding a sudo user for SSH login and removing the root user login over SSH. This article uses the shell (command line terminal) to change the CentOS configuration, based on a minimal CentOS install.
Login and Edit the File sshd_config
To start the process to change the SSH port number, log into the server. Before editing the /etc/ssh/sshd_config file take a copy in case anything goes wrong. Here's the command to copy sshd_config to sshd_cfg_old:
# cp /etc/ssh/sshd_config /etc/ssh/sshd_cfg_old(For all commands in this article only enter the text after the # or $ prompt character, as seen on the terminal screen.)
Editing is done with vi or nano. On a minimal CentOS install, typical for a VPS, nano will not be installed by default. To edit sshd_config using vi:
# vi /etc/ssh/sshd_configOr if logged in as a user with sudo ability:
$ sudo vi /etc/ssh/sshd_configAdd the Required Port Number
Select a new port number above 1024, one that is meaningful to you so it is remembered, or pick a random one. See List of TCP and UDP Port Numbers on Wikipedia. Some admins just double up port numbers, e.g. 22 becomes 2222, but that is familiar to hackers so pick something else, e.g. pick a memorable year and double it. For example 2×1066 is 2132, so port 2132 can be remembered as Twice Battle of Hastings.
The Port line should be in the first page of the file, as either Port 22 or commented out as #Port 22. Go to the line. Press Insert to enter edit mode. Remove the # if present and change the port number to the required value. Press the Esc key to return to command mode and enter :wq to write out the file and quit vi.
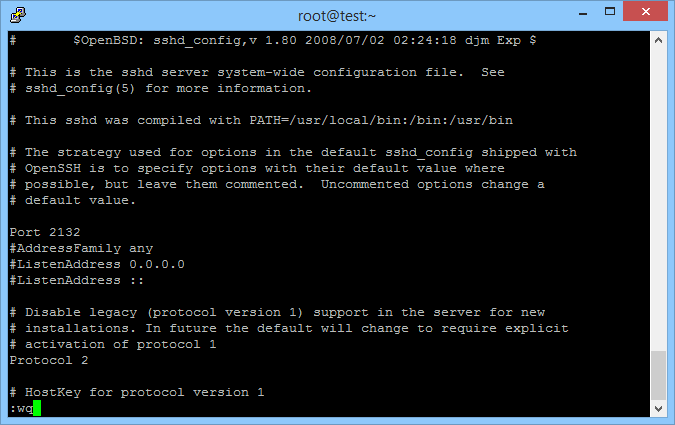
Update SELinux with the New Port Number
If the Security Enhanced Linux module (SELinux) is running then update selinux with the new port number. Failure to update SELinux for the new port will result in a Permission denied showing in the SELinux log. To check that selinux is enabled run sestatus. (In these examples the command is on the first line, and if shown, the result of the command is displayed from the second line onwards, which may differ depending upon your system.):
# sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: enforcing
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Policy version: 28Use semanage to add the new port number to SELinux, see the article RHEL 6: semanage SELinux Command Not Found on how to install the command if not present (e.g. if using the CentOS minimal install). For this article this command was used to check the package for semanage:
# yum provides /usr/sbin/semangeOr:
# yum whatprovides /usr/sbin/semanageAnd this command to install it (remove the -y to manually confirm the install):
# yum -y install policycoreutils-pythonThe port numbers for SELinux can be displayed using a semanage command (pipe to less to page through the list):
# semanage port -l | lessIn the list of ports will be found ssh_port_t tcp 22. Use semanage to add the new port number:
# semanage port -a -t ssh_port_t -p tcp 2132Update Firewall Rules for the New Port Number
In CentOS 6 the firewall is handled by iptables, for CentOS 7 by firewalld. First the newer version of CentOS.
For CentOS 7
The firewalld commands are issued using firewall-cmd. To check that the firewalld service is running use the state option:
# firewall-cmd --state
runningCheck the default zone with get-active-zones (output will be different for other systems):
# firewall-cmd --get-active-zones
public
interfaces: eth0List the rules with list-all:
# firewall-cmd --list-all
public (default, active)
interfaces: eth0
sources:
services: dhcpv6-client ssh
ports: 80/tcp
masquerade: no
forward ports:
icmp-blocks:
rich rules:Add the new port number to the zone, using the permanent option to ensure it survives a system restart:
# firewall-cmd --zone=public --add-port=2132/tcp --permanent
successReload the rules with reload:
# firewall-cmd --reload
successCheck with list-ports:
# firewall-cmd --zone=public --list-ports
80/tcp 2132/tcpFor CentOS 6
The iptables firewall rules are listed using:
# iptables -LThere will be a rule showing that SSH is only allowed on port 22. This needs changing to the new port number. Use vi to open /etc/sysconfig/iptables:
# vi /etc/sysconfig/iptablesGo to this line:
-A INPUT -p tcp -m state –state NEW -m tcp –dport 22 -j ACCEPTChange 22 after –dport to the new port number, e.g. 2132 (press Insert to enter edit mode in vi):
-A INPUT -p tcp -m state –state NEW -m tcp –dport 2132 -j ACCEPTSave and exit (Esc key then :wq). Restart iptables:
# service iptables restartRestart SSH
With the SSH config file changed, SELinux updated and iptables rules updated SSH can be restarted:
For CentOS 7:
# systemctl restart sshd.serviceFor CentOS 6:
# /etc/init.d/sshd restartRestarting CentOS
As an alternative to restarting iptables or reloading firewalld rules, and restarting ssh, restart the the CentOS server:
# rebootor
# shutdown -r nowLogin to CentOS Using SSH to Test The New Port
Using the New SSH Port Number to Access a Remote Server
On a Windows system a program such as PuTTY can be used to access a remote CentOS server using SSH. In this example the port number is 2132. To connect with the new port number enter it in the Port box.
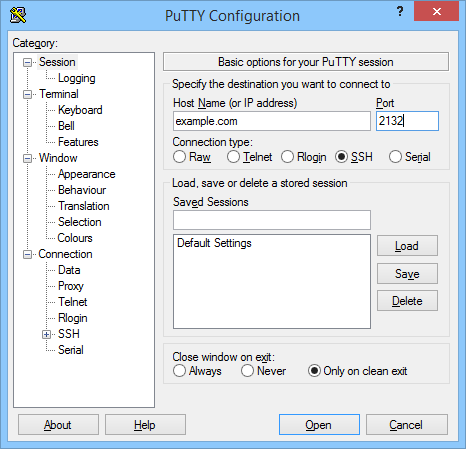
With the host name or IP address also entered select Open. The terminal prompt should appear allowing for a normal login.
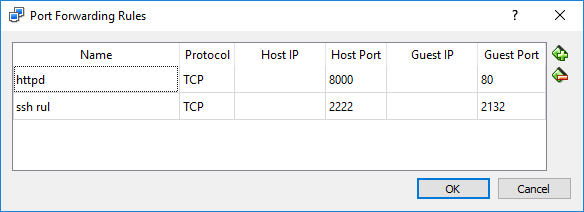
Using the New SSH Port Number to Access a Local Machine VM Server
If accessing a CentOS VPS on a virtual machine on the local computer, you will need to change the Network Address Translation (NAT) port from 22 to the new number. I.e. the 2222 port number, given in the article as an example, entered in PuTTY is now redirected to 2132 instead of 22.
See Also
- Virtualization Software for Windows, Run Another OS for Free
- Virtual CentOS on Windows Using VirtualBox to Run the VM
- SSH into VPS Virtual Machine on Windows Using PuTTY
- Securing OpenSSH on the CentOS Wiki
- List of TCP and UDP Port Numbers on Wikipedia
- View related articles on CentOS and Virtual Private Servers (VPS).
- View the Tek Eye full Index for other articles.
Author:Daniel S. Fowler Published: Updated:







