What is Malware? Malware is Bad for your Computer!
The term malware emerged in the late 1980s and early 1990s as a shortening of the term malicious software. Computer scientists had already been studying computer viruses in the 1970s and 1980s, examining how software viruses damaged computer systems and networks; hence, the term malicious software, which was shortened to the portmanteau "malware". (A portmanteau is a new word made from blending existing words for convenience, novelty, or effect.) Computer hacking and software viruses had become a big issue in the 1980s, resulting in governments introducing new laws to make it illegal to tamper with computers, examples include the Computer Fraud and Abuse Act 1986 in the United States (US) and the Computer Misuse Act 1990 in the United Kingdom (UK).

The Origin of the Term Malware
Yisrael Radai, a computer specialist at the Hebrew University of Jerusalem in Israel, is credited with the first public use of the term "malware". In a Usenet sci.crypt post on July 4, 1990, he wrote the following within a long paragraph within a long discussion on protecting software from viruses, starting with a post titled Need advice on Anti-Viral CRC schem:
"First, it should be noted that since the advent of viruses, Trojans constitute only a very small percentage of malware (a word I just now coined for Trojans, viruses, worms, etc.)." - Yisrael Radai.
From that sentence, it can be seen that malware was categorised under different names, and malicious software had become established in the ever-increasing computerised society. (For further information on Yisrael Radai, see the Appendix at the end of this article.)
- Trojans (or Trojan Horse) - This is malware disguised as a normal piece of software. It is named after the Trojan Horse, which contained hidden soldiers used to break the siege of Troy in Greek mythology. What appears to be a legitimate program may include software that damages a computer. This is why software should only be downloaded and installed from trusted sources.
- Viruses - A computer virus is a type of malware that can spread from one device to another and onwards, propagating malicious software in a similar way to a biological virus like the common cold, influenza, and coronavirus. Someone has to infect a computer with a virus by running an existing infected piece of software. For example, a USB memory stick can hold infected software that a person runs when they plug the stick into a computer. The infected software enters the computer memory and waits for another memory stick to be inserted before copying itself onto the newly inserted USB drive.
- Worms - Malware that does not need human interaction to spread is a worm, usually spreading over computer networks. Worms use vulnerabilities within operating systems and network protocols to transmit themselves to other computers. The malware infection spreads to the other connected computers.
There are other types, variations, and combinations of malware. They exploit weaknesses in computer security and human behaviour.
Although the 1990 Yisrael Radai post is considered the origin of the malware term, it was likely used amongst the people studying computer viruses in the few years prior. I exchanged emails with information security expert Robert Slade. In the email exchange, he stated that he was "using the term in seminars more than a year earlier". Furthermore, the expanded term, "malicious software", can be seen in a 1975 Association for Computing Machinery (ACM) paper and a 1982 computer security curriculum where students are asked to find examples of malicious software:
- Anderson, 1975 - "There is also a software failure-effect problem because processors normally have unrestricted access to the central memory, thus faulty or malicious software can prevent or damage message transactions to which it is not a party."
- Neugent, 1982 - " Many people ignore the threats of wiretapping and malicious software. This may be good policy. Find as many documented cases as you can where these attacks were employed. Draw conclusions."
Hence, malware as a computer security issue is nothing new; we must reinforce the awareness in our cultural memory. This means ensuring that knowledge of the threat from malware is passed on via education, helping people preserve their data, particularly from the threat of ransomware.
Ransomware is a Big Malware Issue
In the 2010s and 2020s, most news items on malware report about companies suffering from ransomware. This is malware that can be highly disruptive to organisations and individuals who rely on computers and software for their business and work. When Ransomware spreads to a computer, it scrambles the data using a secret code and then displays a message demanding payment to unscramble the data. For example, here was the message for the 2017 widely spread WannaCry malware:
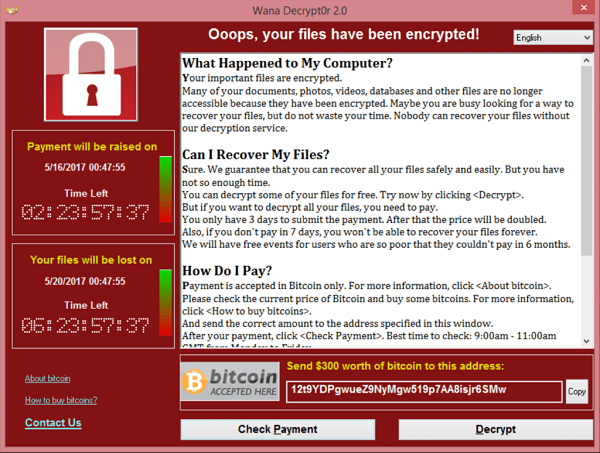
The invention of cryptocurrency, such as Bitcoin, was helpful to cyber criminals, helping them hide the ransom payments people and companies made to get their important data back. The data on computers and devices is valuable. If a criminal can grab all the information from a credit card, they can use it for themselves. They target organisations which keep customer information on databases and run the businesses with computers. A ransomware infection can be costly; hence, the need to keep ransomware out.

Modern computer security is reasonably robust, as long as good practices are followed and multi-factor authentication is used. This is why phishing and other social engineering techniques are problems when trying to prevent malware from infecting a computer:
- Phishing - An email or website pretends to be from a legitimate organisation to get the reader to click on a link or run some software that infects the computer, and then spreads to other computers.
- Social engineering - Cyber criminals will contact individuals and try to manipulate them into revealing usernames, passwords, other security credentials, and confidential information. This can be performed in various ways, including befriending, impersonation, cajoling, and threatening behaviour. Once the required information is obtained, it can be used to gain access to computer systems and install malware.
Malware is a problem for our hyperconnected economies; the list of damaging cyber attacks will only grow as crime is always an arms race between law-abiding society and criminals. However, we can all stay vigilant, stay educated, and follow advice. The UK's National Cyber Security Centre (NCSC), like other governments, has resources for individuals and organisations to help maintain and reduce cybersecurity risks. Individuals must keep operating systems updated, never reveal passwords or codes to anyone else, only run software and visit links you know are from trusted sources, and do not trust random people on the Internet or who call you out of the blue. For organisations, governments often have programs to help them improve cybersecurity; for example, the UK has the Cyber Essentials and Cyber Essentials Plus programs. Becoming security certified is increasingly important to run a resilient and trusted business, helping to win and maintain customers, and protect your computers and devices from malware.
References
- Anderson, George A., and E. Douglas Jensen. "Computer interconnection structures: Taxonomy, characteristics, and examples." ACM Computing Surveys (CSUR) 7.4 (1975): 197-213. DOI: 10.1145/356654.35665
- Neugent, Bill. "A university course in computer security." ACM SIGSAC Review 1.2 (1982): 17-33. DOI: 10.1145/1058230.1058232
- Brunnstein, Klaus, and Fischer-Hübner, Simone and Swimmer, Morton. "Classification of Computer Anomalies." Proceedings of the 13th National Computer Security Conference. Washington, D.C. (1990, 1-4 Oct.): 374-383
Appendix - Yisrael Radai
Yisrael Radai worked in the Computation Center at the Hebrew University of Jerusalem, Israel. He obtained a Master's in Computer Science in 1975 from the University. It was at the Hebrew University when he came into contact with the Israeli PC virus outbreak in January 1988. He subsequently became active in the field of computer virus study, compiling lists of known viruses (Brunnstein, 1990). He joined the editorial advisory board of Virus Bulletin magazine in December 1989. The magazine had only started in July 1989.
Virus Bulletin holds an annual conference, the first of which was held in September 1991. At the 91 conference, Yisrael Radai presented the paper Checksumming Techniques for Anti-Viral Purposes, showing that a Cyclic Redundancy Check (CRC) could be used to aid in protecting data on computer systems from software viruses.
Virus Bulletin magazine reported the sudden death of Yisrael Radai in its June 1996 edition. A short obituary for Yisrael Radai appeared on the comp.virus and alt.comp.virus Usenet groups on 21st May 1996, and the Victoria Free-Net Association (ViFA) website. The obituary was written by information security expert Robert Slade and acknowledged Yisrael Radai's contributions to early computer virus research. Yisrael Radai was 63 years old when he died of a stroke.
Some of the works of Yisrael Radai:
- The Israeli PC virus, 1989, Apr., Computers & Security, 8.2, 111-113. ISSN: 0167-4048. DOI: 10.1016/0167-4048(89)90065-5
- PC/MS-DOS Viruses, 1989, May
- Checksumming Techniques for Anti-Viral Purposes, 1991, Sept. 12-13th, International Virus Bulletin Conference, St. Helier, Jersey.
- The Anti-Viral Software of MS-DOS, 1993 (Available on the Wayback Machine - https://web.archive.org/web/19970711062948/http://www.virusbtn.com/OtherPapers/MSAV/)
- Integrity Checking for Anti-Viral Purposes: Theory and Practice, 1994, Dec. (a revision of his 1991 paper)
- Computer art from the Mandelbrot set, 1996, Nov./Dec., Computers & Graphics, 20.6, 925-926. ISSN: 0097-8493. DOI: 10.1016/S0097-8493(96)00062-3.
See Also
- Timeline of computer viruses and worms
- Morris Worm Attack, Lessons from the First Major Computer Virus
- For a full list of the articles on Tek Eye, see the full site Index.
Author:Daniel S. Fowler Published:







